Maximum flexibility requires maximum responsibility!

Being Agile as an organization and Agile application delivery has been on the radar of many CIO’s and CTO’s trying to reduce the time to market of systems under their control. Often I see agility being interpreted by the other C-levels as a methodology for maximum project flexibility. However maximum flexibility requires maximum responsibility to achieve business value and that is not a solely technical issue, on the contrary!
Being effective in Agile delivery requires a lot of maturity in different areas during project delivery. We will be looking at six axes besides the typical technical one:
- Technical Environment
- Quality Management
- User Experience
- Team Dynamics
- Ownership Management
- Project Management
- Company’s Eco-System
To generate maximum value, the Agile methodology has guiding principles and these have to be translated in operating procedures. Based on earlier work of M. Balbes, we propose a model to quantify this operational effectiveness by scoring a list of required capabilities according to maturity going from no capabilities to innovating and leading capabilities.
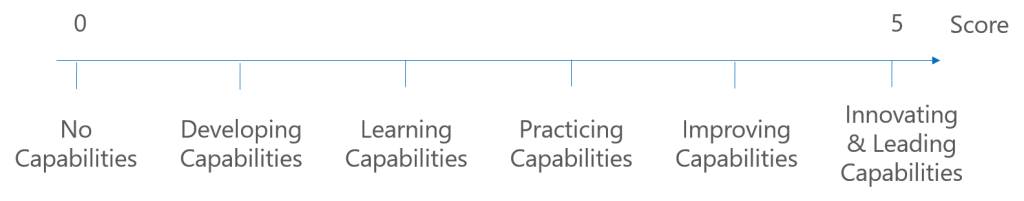
An Excel version to score your organization can be downloaded here:
Before we try to measure something, what are the Agile principles companies should adhere to?
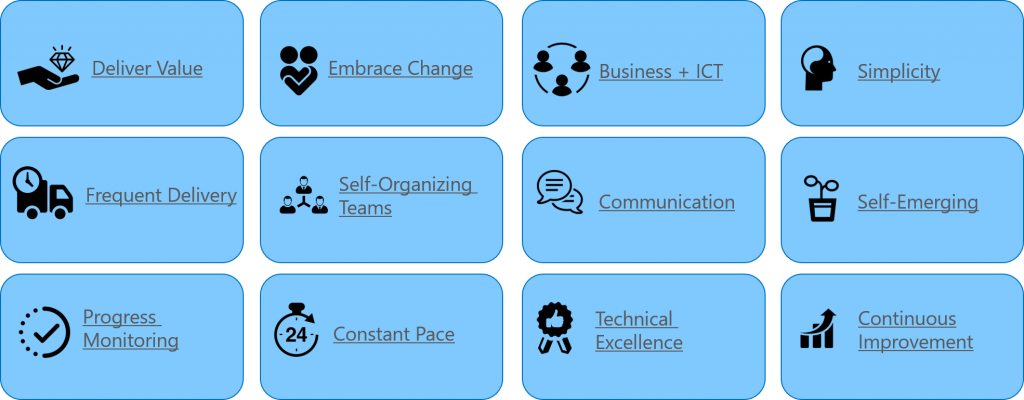
- Delivery Value: Focus on continuously delivery value to the customer, key-users …
- Embrace Change: Change is good and inevitable. Change avoids waste by adapting before it is too late.
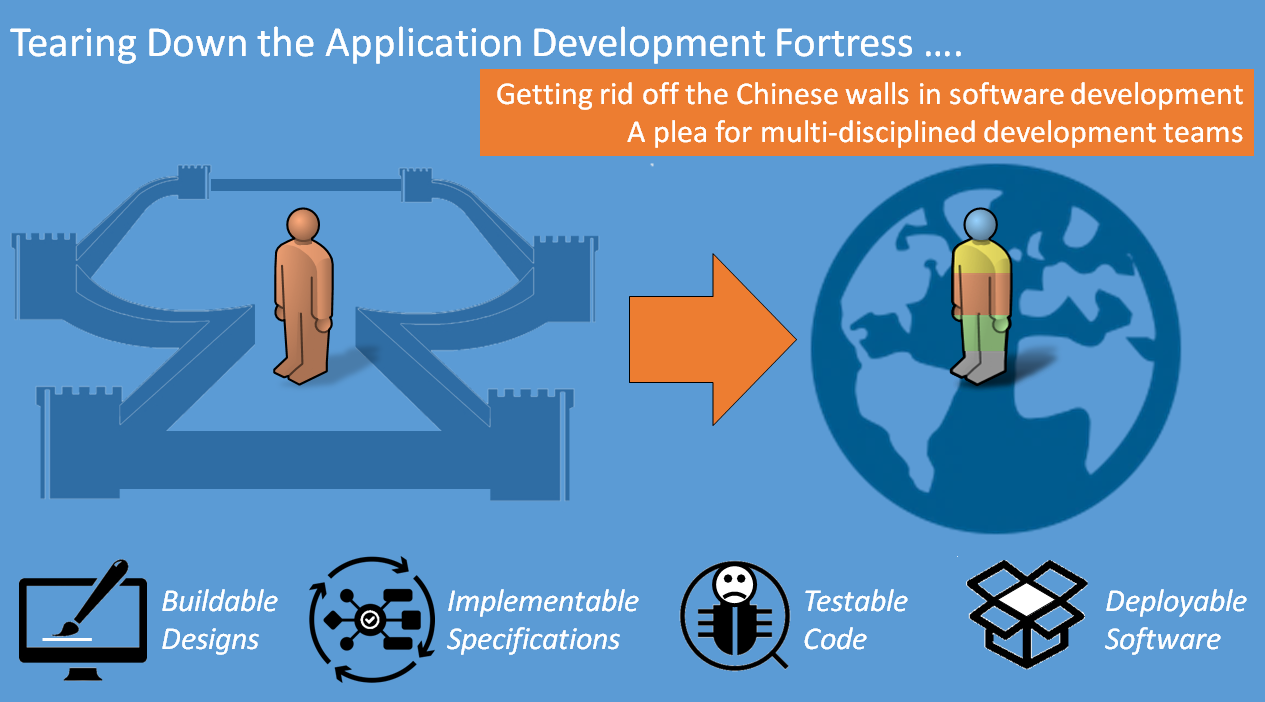
- Business + ICT: Avoid Chinese walls between teams. Work closely together every day.
- Simplicity: Focusing on what is good enough to avoid gold-plating. Work smarter not harder.
- Frequent Delivery: Delivery version frequently to have short feedback cycles.
- Self-Organizing Teams: Motivated individuals will be able to identify how to organize the work and what they need.
- Communication: Transparent, open and face-to-face communication helps insights and clear understanding.
- Self-Emerging: Avoid analysis-paralysis and big design up-front. Design for what is needed now and adapt.
- Progress Monitoring: Measure progress as delivered software i.e. potential shippable product increments.
- Constant Pace: The team should work according at a pace they can keep up without feeling pressured.
- Technical Excellence: Focus on the quality of artefacts and development process.
- Continuous Improvement: Be self-reflective and make incremental improvements to the development process.
For the different axes an organization needs to have some capabilities in place and below some examples of these capabilities. The detailed list can be found in the attached Excel model.
Technical Environment capabilities check if the principles of extreme programming are enabled. What is the company’s maturity for following capabilities:

- Unit testing, test driven development and technical testing approaches
- Continuous integration methods
- Pair programming – Spikes experimentation
- Source control – Branching strategy approaches
- Release management
- Coding standards usage
- Development process – Software Development Life Cycle
- Shared code ownership
- Software changeability enablement
Quality Management validates if quality assurance is taken in favor of quality measurement. What is the company’ maturity for following capabilities:

- Quality management process
- Code Quality – Internal – External Quality impact analysis
- Team’s ownership of quality
- Defect management
- User acceptance testing – Exploratory testing
User Experience looks at the application of multi-disciplinary teams since developers are not designers. What is the company’s maturity for following capabilities:

- Graphical Design – UX selection process
- Embedded usability testing
Team Dynamics focuses how people collaborate and how self-reflective they are. What is the company’s maturity for following capabilities:

- Team Structure – Charter agreements
- Team discussion – Conflict resolution processes
- Retrospectives – Stand-Ups organizations
- Information radiators availability
- Continuous improvements
- Change acceptance process
Ownership Management goal is to see how well the link between business and IT is managed to enhance a project’s business value. What is the company’ maturity for following capabilities:

- Identified stakeholders management
- User stories – Story sizing principles
- Acceptance criteria – Owner acceptance process
- Delivering value – User feedback management
- Prioritization – Backlog – Release Cadence organization
- Backlog – Change management
Project Management looks for transparency in reporting and collaboration enhancement. What is the company’s maturity for following capabilities:
- Kaban – Milestones overview
- Decisions – Meeting minutes creation
- Staffing alignment
Finally we have the company’s Eco-System or the environment. What is the company’s maturity for following capabilities:

- Risk Identification – Monitoring – Mitigation
- Embedded learning culture
- Change – Champions creation and management
- Governance – Internal Change – External Change management
An overview presentation can be downloaded here: