Below I present a basic overview of firewall architecture. I created this as a reference document in the case the LAN-guys are barking network stuff to me on a project I’m working on.
The untrusted network in the diagrams you can interpret as the Internet and the trusted network you can read as the intranet or the company’s LAN.
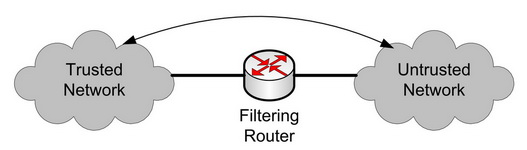
The Packet Filtering Router screens the packets exchanged between the untrusted and trusted network. Basic routers cannot do much more then routing traffic and do only support basic rulesets. Basic rules are for example indentifying subsets of ip-addresses that are allowed to communicate between the untrusted and trusted network.
More elaborate rulesets allow for filtering based on the detailed content of the ip-packages. In the latter case the router is sometimes called a firewall.
Bastion Host or Screened Host
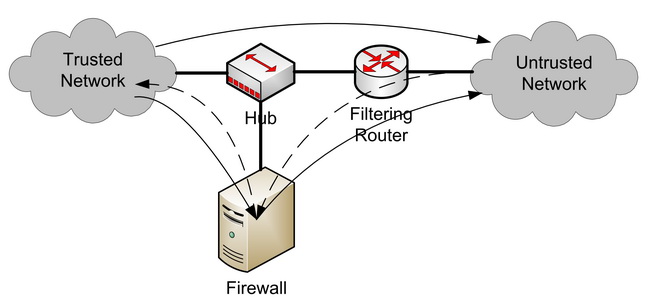
Incomming traffic, from the untrusted network, is forwarded to the bastion host server or firewall that will determine whether or not the messages are forwarded to the trusted network.
Outgoing communication can follow the reversed route or can go directly from the trusted to the untrusted network bypassing the bastion host.
Dual-Homed Gateway
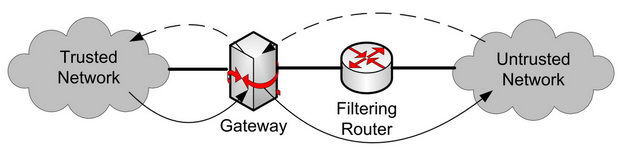
The gateway has two network interfaces and sits between the trusted and untrusted network. Direct forwarding on the network interfaces is blocked to force the traffic to go through an application or proxy running on the gateway. The application will connect to the two networks.
Demilitarized Zone (DMZ) or Screened Subnet
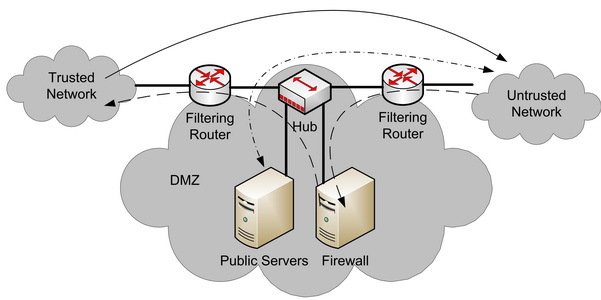
Here we have a set of two routers creating an additional network, in between the trusted and untrusted network, called the DMZ.
The traffic destined from the trusted network to the untrusted network is routed directly through the two routers or goes to the firewall and is forwarded to the untrusted network from there.
Traffic from the untrusted network to the trusted network is sent first to the firewall in the DMZ and is then forwarded to the trusted network.
Public accessible servers (for example webservers) are located in the DMZ and the traffic is routed from the untrusted network directly to those servers.
The major difference between this architecture and the Bastion Host is that the Bastion Host would have had to combine the functionality ran on the public servers and the traffic forwarding functionality.
Firewall Appliance
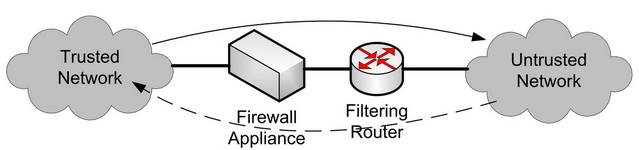
This is piece of hardware with multiple network interfaces that allows it to connect to multiple subnets, i.e. the gateway functionality like with dual-home gateway, and do intelligent packet filtering.
Proxy
If the traffic from the trusted network to the untrusted network is forced to go through one location in the DMZ, it is possible to introduce some additional functionality like:
- hiding the ip-addresses from clients in the untrusted network (anonymizing requests)
- caching request from multiple client in the trusted network to the same source in the untrusted network
If the proxy does this in such a way that exchanged messages are not modified, we say it is a tunneling proxy sometimes called a gateway.
Some of the proxies are transparent for the client in the untrusted network. This has the advantage that the clients are unaware of it and do not require any configuration. For anonymization this is not possible because the proxy needs to modify the message exchanged between the trusted and untrusted network.
Reverse Proxy
Here a proxy is acting on traffic coming from the untrusted network destined to the public accessible servers in the DMZ. The reverse proxy can provide following additional functionality transparently for the clients in the untrusted network:
- load balancing the incoming request transparently over multiple servers
- terminating secure communication or decrypting encrypted messages, to take away this burden from the public accessible servers behind it
- caching frequently requested information