In a pervious article we talked about evolving Citizen Developers from City Dwellers to Townsmen … so they can become first class citizen. We discussed the left-shift of responsibilities from pro-developers to Citizen Developers and explained that Low-Code / No-Code (L-C/N-C) platforms cannot exonerate an organization of all the responsibilities shifted to these Citizen Developers:
It is the tooling support of the L-C/N-C platforms
that evolve Citizen Developers from City Dwellers to Townsmen.
It is the organization’s (city) strategy and tactical focus
that turns them into first class citizens.
Next we introduced 3 prerequisites for success the so-called D^3 or Data, Devices and Delivery.
After some more research it became clear that still some dimensions were missing to cover all the angels of people – processes – technology.
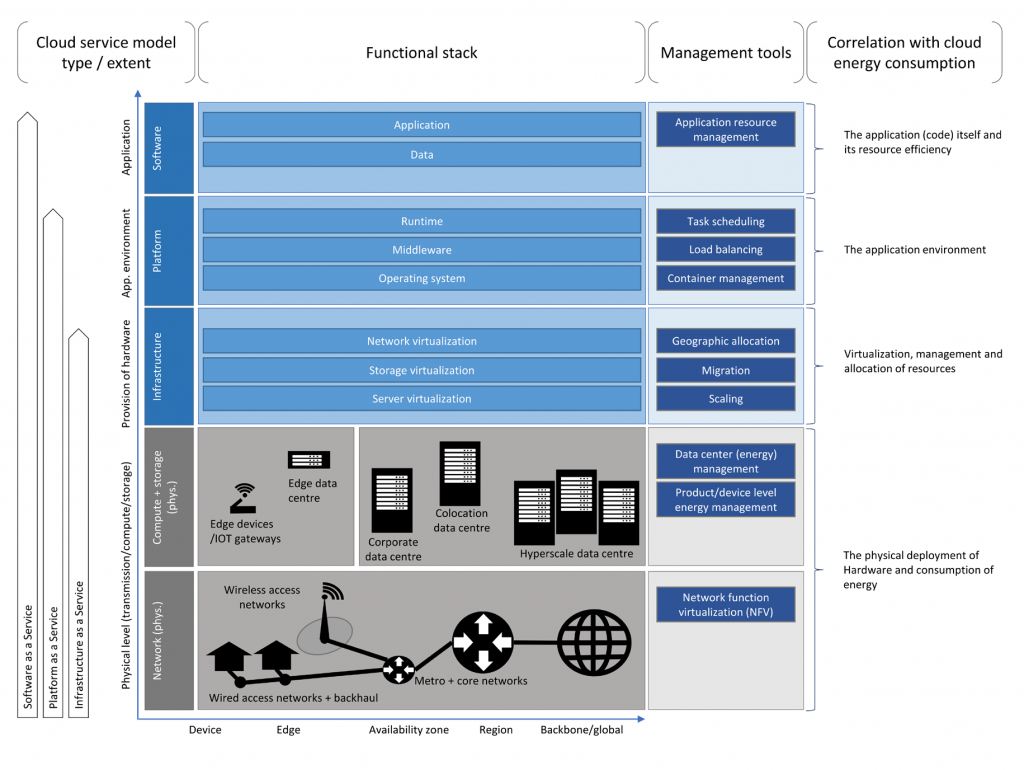
Firstly, we want to extend Data with Digitalization. Data is a necessary but not a sufficient condition. Data as a collection of information is nothing without a clear view where it fits within business processes. It is here where Digitalization comes in to add the process angle as sufficient condition.
Secondly, in order to have an acceptable ROI for a L-C/N-C platform investment, a high level of reusability is important. Reusability focusses on technical building blocks like components and connections but also on governance and policies. The idea that there are things that will be application-specific and handled by a Citizen Developer and other things will be generic and handled on an organizational level, introduces a dimension where we look at the distribution of reusable elements throughout the L-C/N-C platform.
The two additions mean that we have now D^5 model:
Data – Devices – Delivery – Digitalization – Distribution
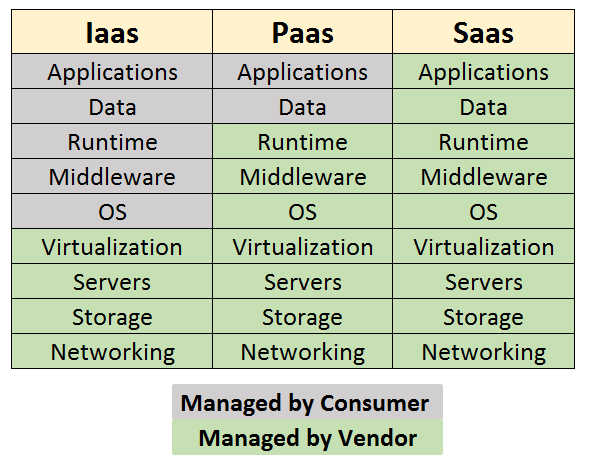
Data: data encapsulation/exposure is a prerequisite

For a Citizen Developer to develop applications for his business,
he needs access to his business data
- Data source isolation: data specific for his business
- Data availability: data accessible through API’s
- Data storage: data to be stored in relation to his application
Devices: suitable devices are a prerequisite

For a Citizen Developer to build applications,
he needs to be able to select a suitable device for the problem at hand
i.e. desktop, mobile, VR-AR, kiosk
- Device availability: devices made available on short-term to all the users of his application
- Device/License sharing: devices and licenses ad-hoc attributed and revoked to users
- Device security policies: devices are managed to protect against exposure and loss of business data
Delivery (Deployment): platform governance and strategy is a prerequisite

For a Citizen Developer to manage the life cycle of his application,
he needs to be able to count on supporting process to be in place
- Application Delivery TOM/SOM: application delivery processes clearly describe roles and responsibilities for Business and IT
- Delivered Application Support Model: delivered application he can support directly or indirectly
- Application DevSecOps policies: business risks and IT risks are controlled by DevSecOps tooling
Digitalization: process oriented automation is a prerequisite

For a Citizen Developer to contribute to the digitalization
he needs to be able to affect end-to-end processes he owns
- Monetized Digitalization: processes direct and indirect costs and revenues are quantified (FinOps)
- Dematerialized Digitalization: processes descriptions focus on activities (steps towards end-results) before information (content carried between activities)
- Optimized Digitalization : end-to-end processes are defined as a set of interrelated activities (process optimization not isolated activity optimization)
Distribution: availability of reusable building blocks is a perquisite

For a Citizen Developer to efficiently assembly his application
he needs to combine distributed building blocks
- Distributed Components: reusable front-end components (UI elements) as well as reusable back-end components (Systems/Solutions)
- Distributed Connectivity: reusable means of integration between components (data exchange, network connectivity, import/export)
- Distributed Responsibilities: reusable cross application responsibilities (generic governance) extending application specific responsibilities of his application (app specific governance)


 ALM risks: keeping the application up to date through evolving the requirements, architecture and technology of the application to protect against functional obsoleteness and technical debt.
ALM risks: keeping the application up to date through evolving the requirements, architecture and technology of the application to protect against functional obsoleteness and technical debt. Security Risks: keeping the application secure and protect against incorrect access, usage and data exposure.
Security Risks: keeping the application secure and protect against incorrect access, usage and data exposure. Costs Risks: baring the cost of the application and protect against inefficient and uncontrolled spending
Costs Risks: baring the cost of the application and protect against inefficient and uncontrolled spending Governance Risks: ensure the application is managed as part of a solution architecture landscape
Governance Risks: ensure the application is managed as part of a solution architecture landscape Strategic Risks: Citizen developer’s focus limited to ad-hoc problem solving i.e. operational problems, forgetting about tactical and strategic long-term solutions. Missed opportunities towards generalization and standardization of solutions leading to redundancy/duplication: excess costs and limited scaling.
Strategic Risks: Citizen developer’s focus limited to ad-hoc problem solving i.e. operational problems, forgetting about tactical and strategic long-term solutions. Missed opportunities towards generalization and standardization of solutions leading to redundancy/duplication: excess costs and limited scaling. Process Risks: Citizen developer’s focus on a part of a business process (one or more activities) resulting in sub-optimal solutions. Automating an inefficient process or part of a process results in an automated inefficiency. It requires an end-to-end process view and level of abstraction beyond the problem at hand to create efficient solutions.
Process Risks: Citizen developer’s focus on a part of a business process (one or more activities) resulting in sub-optimal solutions. Automating an inefficient process or part of a process results in an automated inefficiency. It requires an end-to-end process view and level of abstraction beyond the problem at hand to create efficient solutions. Obsolesce Risks: Citizen developers applying a technology because they can, not because it is the right thing to do: “If you have a hammer everything looks like a nail“. Limited critical reflection on why and when to apply a technology. Lack of understanding of correct usage and limitation of a technology.
Obsolesce Risks: Citizen developers applying a technology because they can, not because it is the right thing to do: “If you have a hammer everything looks like a nail“. Limited critical reflection on why and when to apply a technology. Lack of understanding of correct usage and limitation of a technology.  Regulatory Risks: Citizen developers’ focus solely on the business process forgetting about regulatory compliance e.g. data usage (GDPR, data privacy) and security (data leakage and data loss). Limited understanding of requirements beyond functional requirements omitting domain and non-functional requirements. Limited accountability toward end-to-end process and compliance of activities part of an end-to-end process.
Regulatory Risks: Citizen developers’ focus solely on the business process forgetting about regulatory compliance e.g. data usage (GDPR, data privacy) and security (data leakage and data loss). Limited understanding of requirements beyond functional requirements omitting domain and non-functional requirements. Limited accountability toward end-to-end process and compliance of activities part of an end-to-end process.